If you want to omit passphrase and password entry when you are using Secure Shell, you can use the agent daemon. Use the ssh-agent command at the beginning of the session. Then, store your private keys with the agent by using ssh-add. If you have different accounts on different hosts, add those keys that you intend to use in the session. The ssh-agent is a helper program that keeps track of user's identity keys and their passphrases. The agent can then use the keys to log into other servers without having the user type in a password or passphrase again. This implements a form of single sign-on (SSO). The SSH agent is used for SSH public key authentication. Setup the SSH authentication agent # Start the agent eval `ssh-agent` # Add the identity (private key) to the agent ssh-add /path/to/private-key # Enter key passphrase (one time only, while the agent is running). For an introduction to SSH and how SSH keys work, see SSH Essentials: Working with SSH Servers, Clients, and Keys. Password-less access works only when you connect to your target system from your host development system with a matching private SSH key.
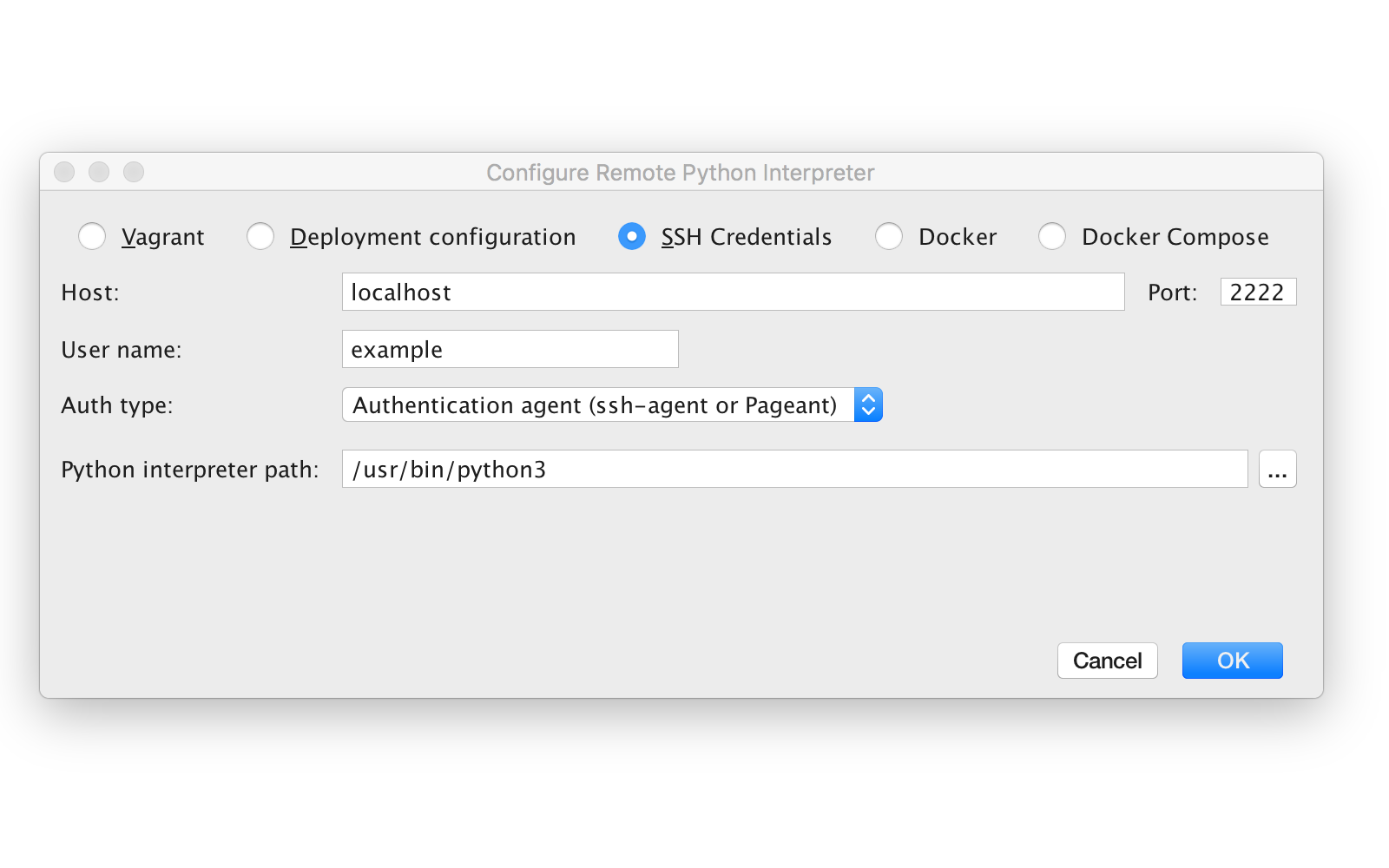
Secure Shell (SSH) allows you to remotely administer and configure your Windows IoT Core device
Using the Windows 10 OpenSSH client
Important
The Windows OpenSSH client requires that your SSH client host OS is Windows 10 version 1803(17134). Also, the Windows 10 IoT Core device must be running RS5 Windows Insider Preview release 17723 or greater.
The OpenSSH Client was added to Windows 10 in 1803 (build 17134) as an optional feature. To install the client, you can search for Manage Optional Features in Windows 10 settings. If the OpenSSH Client is not listed in the list of installed features, then choose Add a feature.
1password Ssh Agent Download
Next select OpenSSH Client in the list and click Install.
To login with a username and password use the following command:
Where host is either the IP address of the Windows IoT Core device or the device name.
The first time you connect you see a message like the following:
Type yes and press enter.
If you need to login as DefaultAccount rather than as administrator, you will need to generate a key and use the key to login. From the desktop that you intend to connect to your IoT Device from, open a PowerShell window and change to your personal data folder (e.g cd ~)
Register the key with ssh-agent (optional, for single sign-on experience). Note that ssh-add must be performed from a folder that is ACL'd to you as the signed-in user (BuiltinAdministrators and the NT_AUTHORITYSystem user are also ok). By default cd ~ from PowerShell should be sufficient as shown below.
Tip
If you receive a message that the ssh-agent service is disabled you can enable it with sc.exe config ssh-agent start=auto
To enable single sign, append the public key to the Windows IoT Core device authorized_keys file. Or if you only have one key you copy the public key file to the remote authorized_keys file.
If the key is not registered with ssh-agent, it must be specified on the command line to login:
If the private key is registered with ssh-agent, then you only need to specify DefaultAccount@host:
The first time you connect you see a message like the following:
Type yes and press enter.
You should now be connected as DefaultAccount
To use single sign-on with the administrator account, append your public key to c:dataProgramDatasshadministrators_authorized_keys on the Windows IoT Core device.
You will also need to set the ACL for administrators_authorized_keys to match the ACL of ssh_host_dsa_key in the same directory.
To set the ACL using PowerShell
Note
If you see a REMOTE HOST IDENTIFICATION CHANGED message after making changes to the Windows 10 IoT Core device, then edit C:Users<username>.sshknown_hosts and remove the host that has changed.
See also: Win32-OpenSSH
Using PuTTY
Download an SSH client
In order to connect to your device using SSH, you'll first need to download an SSH client, such as PuTTY.
1password Ssh Agent
Connect to your device
1password Ssh Agent Sign In
In order to connect to your device, you need to first get the IP address of the device. After booting your Windows IoT Core device, an IP address will be shown on the screen attached to the device:
Now launch PuTTY and enter the IP address in the
Host Nametext box and make sure theSSHradio button is selected. Then clickOpen.If you're connecting to your device for the first time from your computer, you may see the following security alert. Just click
Yesto continue.If the connection was successful, you should see
login as:on the screen, prompting you to login.
EnterAdministratorand press enter. Then enter the default passwordp@ssw0rdas the password and press enter.If you were able to login successfully, you should see something like this:
Update account password
It is highly recommended that you update the default password for the Administrator account.
To do this, enter the following command in the PuTTY console, replacing [new password] with a strong password:
Configure your Windows IoT Core device
To be able to deploy applications from Visual Studio 2017, you will need to make sure the Visual Studio Remote Debugger is running on your Windows IoT Core device. The remote debugger should launch automatically at machine boot time. To double check, use the tlist command to list all the running processes from PowerShell. There should be two instances of msvsmon.exe running on the device.
It is possible for the Visual Studio Remote Debugger to time out after long periods of inactivity. If Visual Studio cannot connect to your Windows IoT Core device, try rebooting the device.
If you want, you can also rename your device. To change the 'computer name', use the
setcomputernameutility:
You will need to reboot the device for the change to take effect. You can use the shutdown command as follows:
Commonly used utilities
See the Command Line Utils page for a list of commands and utilities you can use with SSH.
Ssh Agent Windows
In Unix, ssh-agent is a background program that handles passwords for SSH private keys. The ssh-add command prompts the user for a private key password and adds it to the list maintained by ssh-agent. Once you add a password to ssh-agent, you will not be prompted for it when using SSH or scp to connect to hosts with your public key.
The public part of the key loaded into the agent must be put on the target system in ~/.ssh/authorized_keys; see Set up SSH public key authentication to connect to a remote system.
To use ssh-agent and ssh-add, follow the steps below:
- At the Unix prompt, enter:
Make sure you use the backquote (
`), located under the tilde (~), rather than the single quote ('). - Enter the command:
- Enter your private key password.
- When you log out, enter the command: To run this command automatically when you log out, place it in your
.logoutfile (if you are usingcshortcsh) or your.bash_logoutfile (if you are usingbash).
ssh-agent2 and ssh-add2, are the same as outlined above. To use them, follow the instructions above, replacing all occurrences of ssh-agent with ssh-agent2, and ssh-add with ssh-add2. The SSH2 versions will only work if both your computer and the remote host are running SSH2.1password Ssh Agent Portal
At Indiana University, for personal or departmental Linux or Unix systems support, see Get help for Linux or Unix at IU.
